Connect to AWS
Connecting Nullstone to your AWS account is necessary for Nullstone to manage your infrastructure. Nullstone provides two methods for access: Assumed Role and Access Keys. AWS and Nullstone recommend using Assumed Role to delegate access.
Assume Role
In the Assume Role pattern, an admin creates a role in the target AWS account granting explicit access to a single AWS account. Nullstone generates an "External ID" and shares with the admin to enhance the trust relationship. We created and secured an AWS account (Account ID: 875119311270) dedicated to only assuming role. Our software engineers do not have access to this account. At any point, you can remove the role from your AWS account which revokes access to Nullstone.
TIP
For more details from AWS, see How to use an external ID when granting access to your AWS resources to a third party.
You can configure this through AWS management console or through the CLI.
CLI
WARNING
In order to use the CLI, you must configure your terminal with access to the target AWS account. See Installing the AWS CLI and Configuring the AWS CLI for more information.
Create a file assume-role-policy.json with the following content. Make sure to insert the external ID into the document generated from the Nullstone UI.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::875119311270:root"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "(Insert nullstone-generated external ID)"
}
}
}
]
}Now, let's create the role using the assume role policy document. This is the piece that allows Nullstone to gain necessary access.
aws iam create-role --role-name nullstone --assume-role-policy-document file://assume-role-policy.jsonTo finish, let's give this role access to provision infrastructure on your behalf.
aws iam attach-role-policy --role-name nullstone --policy-arn arn:aws:iam::aws:policy/AdministratorAccessFINISH
Return to the Nullstone UI and Test Connection before proceeding.
Management console
Follow this link to begin creating a role for "Another AWS account": https://console.aws.amazon.com/iam/home?region=us-east-1#/roles$new?step=type&roleType=crossAccount.
On that page, set the Account ID to 875119311270. Check "Require external ID" and copy the External ID from Nullstone UI into the AWS UI. When done, click "Next: Permissions".
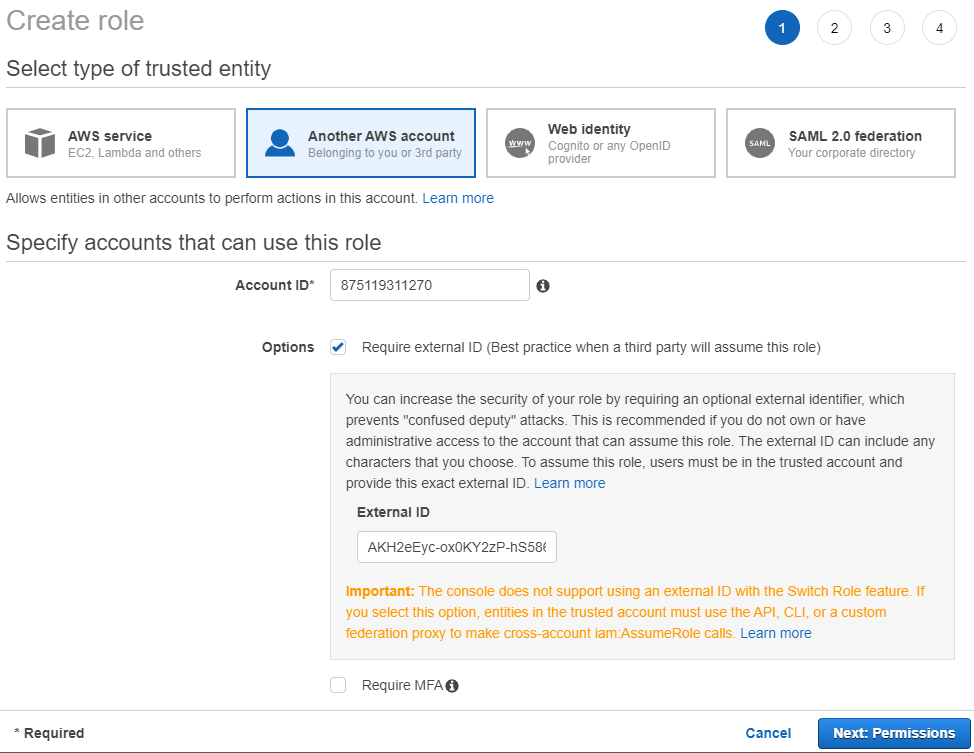
Next, we are going to give this role access to provision infrastructure on your behalf. Select "Administrator Access" and click "Next: Tags".
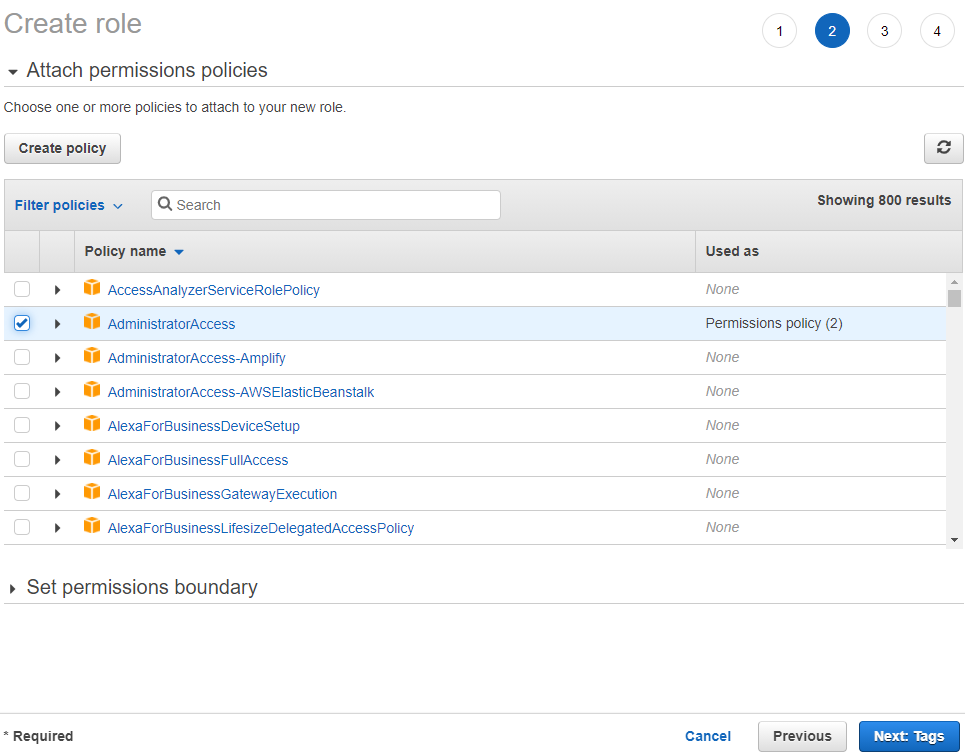
If your organization has a policy of adding explicit tags, feel free to add tags on the following screen. When done, click "Next: Review".
On the next screen, enter the Role name nullstone. Click "Create Role" to finish the process.

FINISH
Return to the Nullstone UI and Test Connection before proceeding.
Access Keys
CLI
Access Keys support is coming soon!
Management console
Access Keys support is coming soon!